The Kanakuk Child Protection Philosophy
The Kanakuk Child Protection Plan establishes direct and indirect defense measures to combat the very nature of abusers, and the tactics used to infiltrate youth organizations and victimize children. Ultimately, the CPP is designed to:
- Prevent would-be molesters from gaining isolated access to minors
- Detect behavior patterns and early-stage abuse tactics, and resolve prior to an inappropriate occurrence.
- Respond promptly and effectively to suspicions or allegations of child sexual abuse

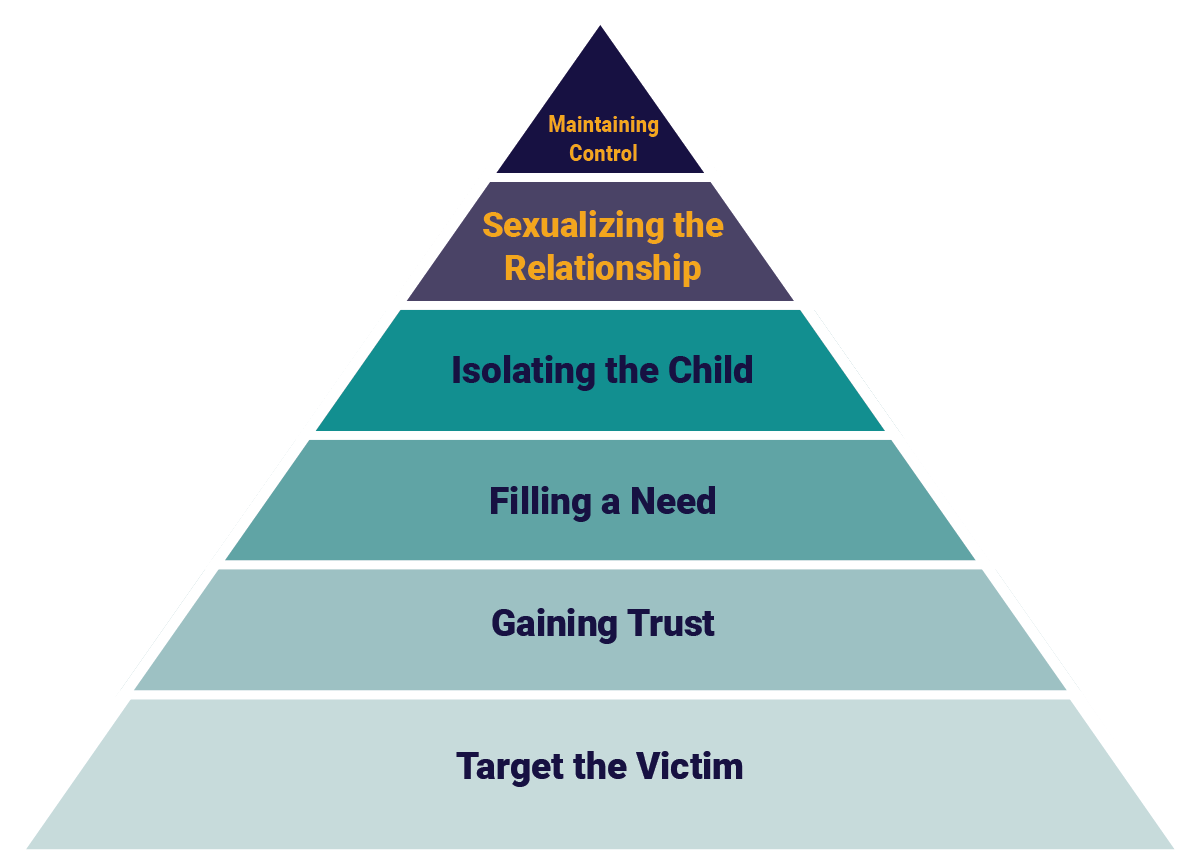
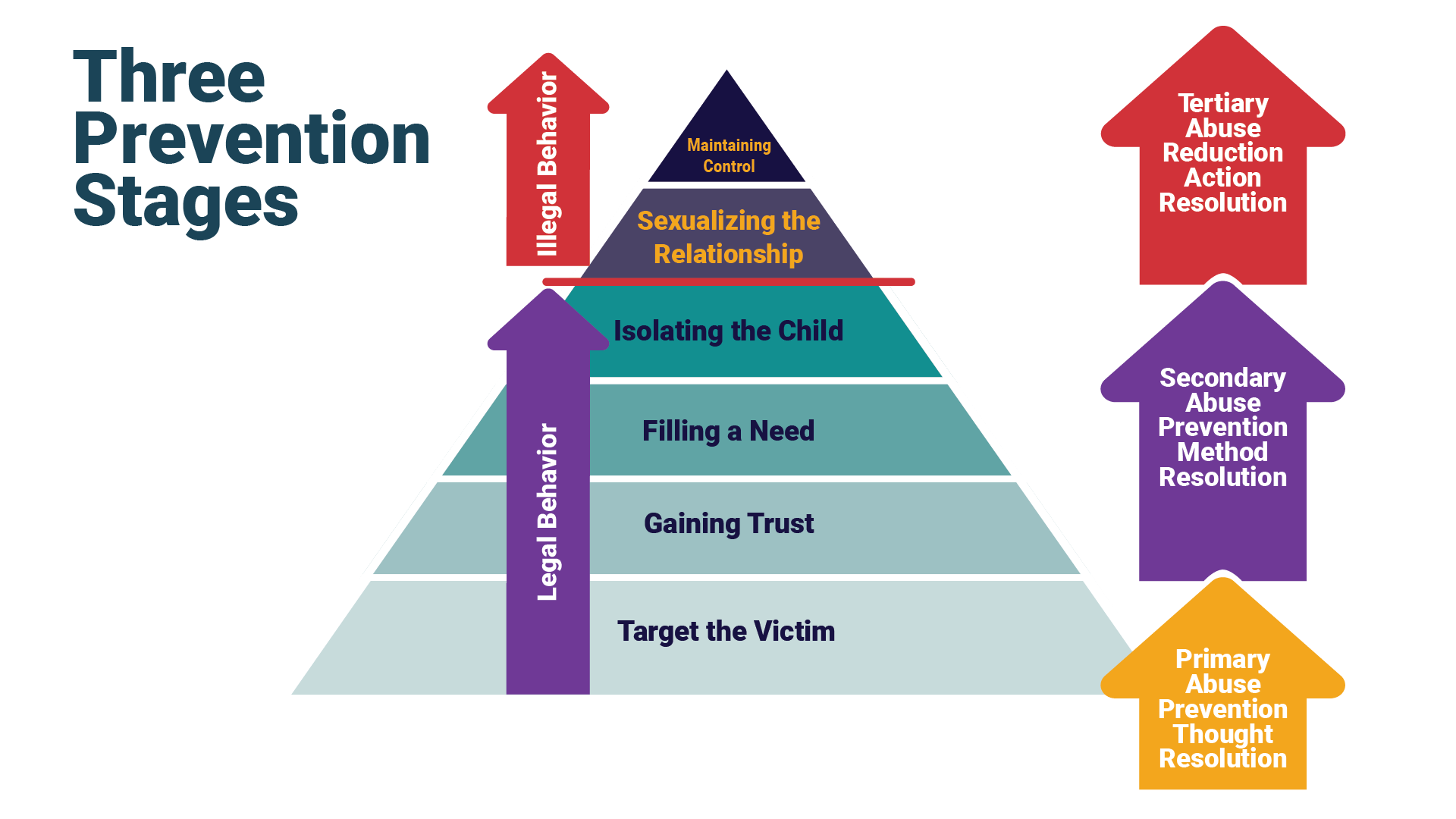
 True Prevention Corridor: The True Prevention Corridor (TPC) denotes the span of time between peer/peer or adult/child appropriate interaction leading to illegal behavior. (See purple shaded area below). The TPC may span minutes, hours, days, weeks or even months, and is subject to the type of molester (see above), the method of grooming and boundary reduction, the vulnerability of victims, and the effectiveness of parental or organizational child protective measures.
True Prevention Corridor: The True Prevention Corridor (TPC) denotes the span of time between peer/peer or adult/child appropriate interaction leading to illegal behavior. (See purple shaded area below). The TPC may span minutes, hours, days, weeks or even months, and is subject to the type of molester (see above), the method of grooming and boundary reduction, the vulnerability of victims, and the effectiveness of parental or organizational child protective measures.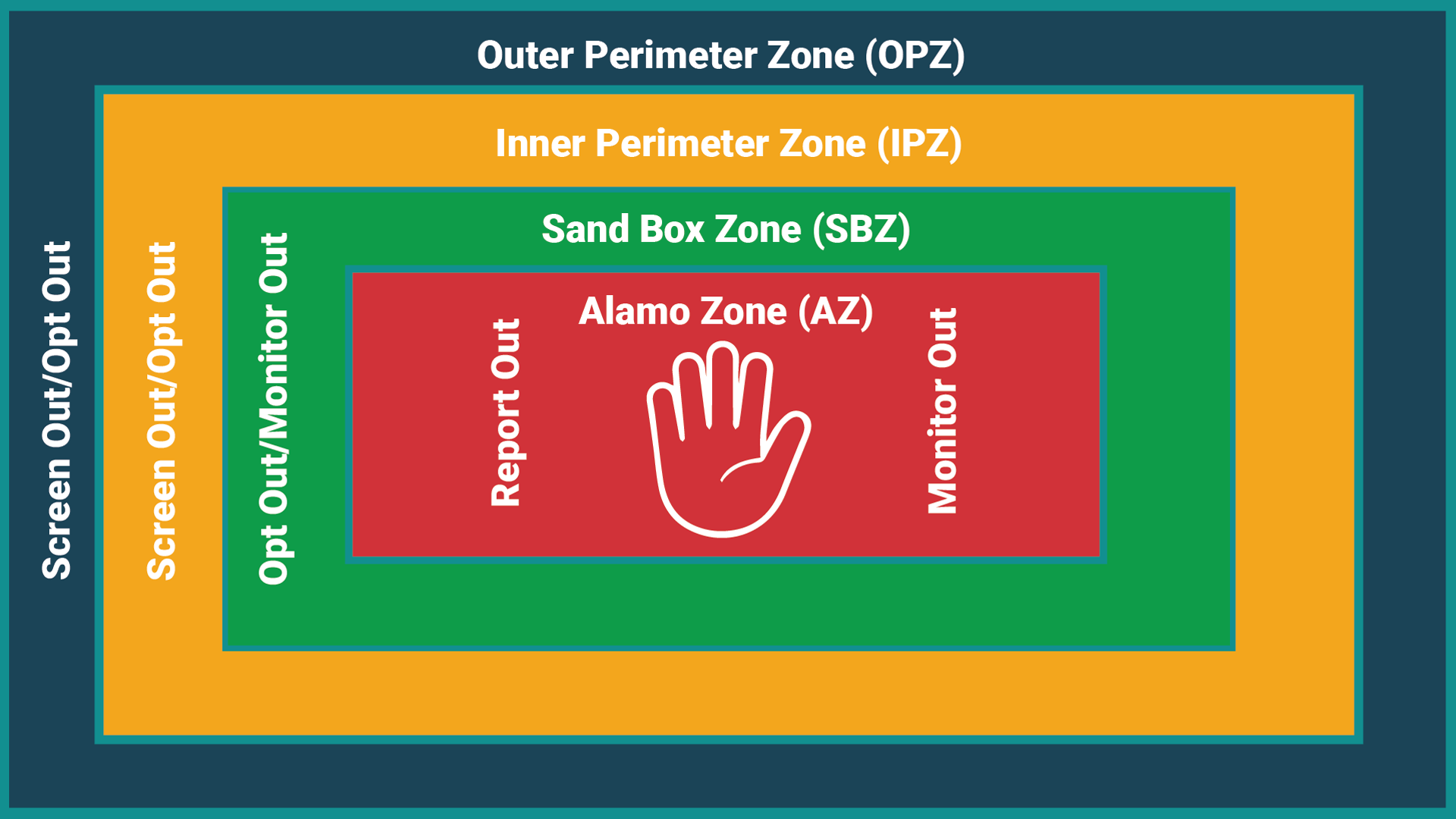
 The Kanakuk Abuser Threat Indicator identifies positions or roles within a youth serving organization that may pose a greater threat to minors based on their degree of access and control. The greater the access or control of a position or role, the higher the Threat Level Score (TLS). The TLS score is derived from a series of eight questions based on degrees of access or control. Finally, based on the Threat Level Score, the youth organization can then focus resources on these higher threats as it relates to hiring, training and monitoring.
The Kanakuk Abuser Threat Indicator identifies positions or roles within a youth serving organization that may pose a greater threat to minors based on their degree of access and control. The greater the access or control of a position or role, the higher the Threat Level Score (TLS). The TLS score is derived from a series of eight questions based on degrees of access or control. Finally, based on the Threat Level Score, the youth organization can then focus resources on these higher threats as it relates to hiring, training and monitoring.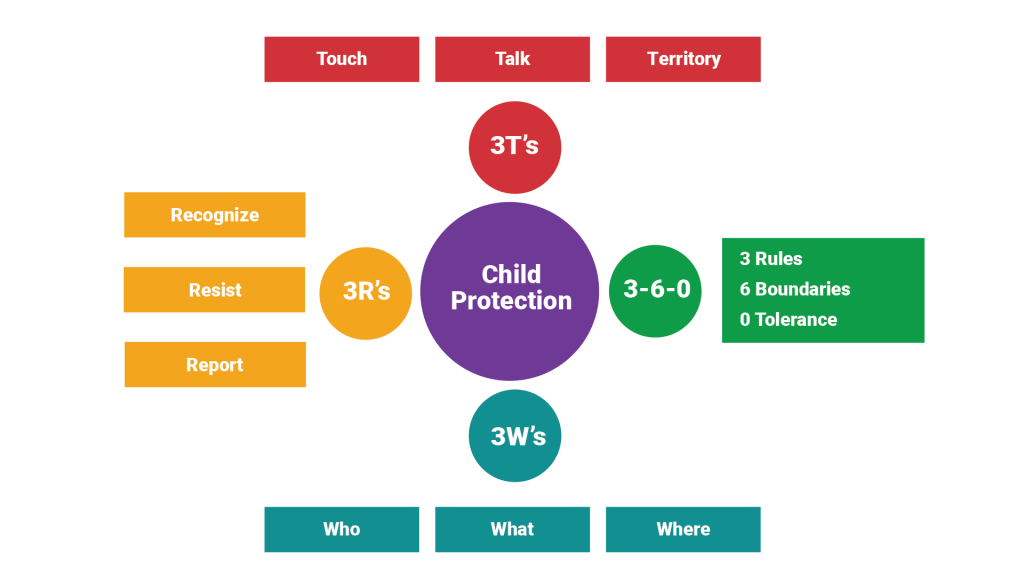 Touch/Talk/Territory (3 T’s)
Touch/Talk/Territory (3 T’s) EyeShot Theory training and inspection for the protection of visibility where private areas are mandatory (cabins, bathrooms), and the promotion of visibility where privacy is unnecessary (sheds, offices, meeting rooms, etc).
EyeShot Theory training and inspection for the protection of visibility where private areas are mandatory (cabins, bathrooms), and the promotion of visibility where privacy is unnecessary (sheds, offices, meeting rooms, etc).